Demystifying DoS and DDOS Attacks and Securing Your Computer
We often hear about DDoS and DoS attacks such as the one that hit Amazon Web Services back in February – which the company says was the largest DDoS attack in recorded history and which it mitigated successfully.
But it's not enough to just hear about these attacks and then forget about them. By becoming more aware about the kind of attacks cybercriminals launch, you can protect your computer better. This knowledge leads to better data security, which means your personal, critical, and sensitive information doesn't pass into the hands of criminals.
So: how do DDoS attacks and DoS attacks differ from one another?
When it comes how intimidating modern day cyberattacks, Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks take the cake and eat it too. A successful attack can cost an organization big money, and the reputational damage caused is tremendous. While most attacks have an eye on sensitive organizational data, many are also used by ‘foreign actors' to cripple essential services in another country.
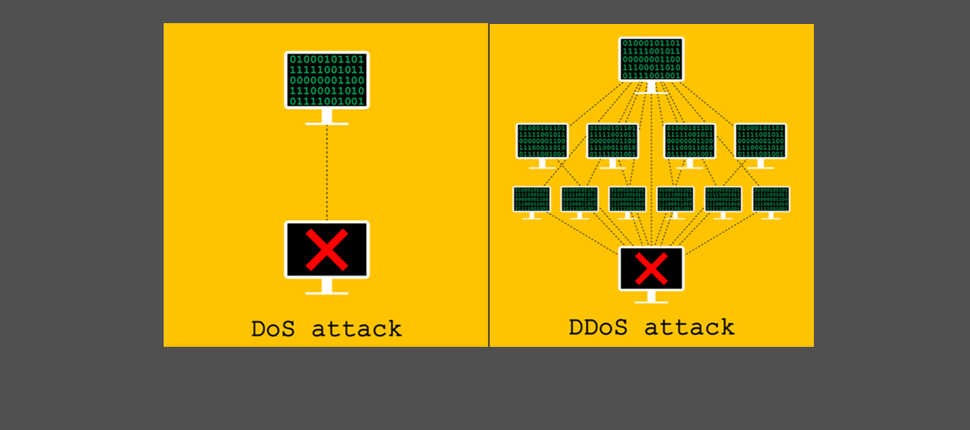
What is are DoS attacks?
The core objective of a DoS attack is to shut down a network, system, or machine. What this means is that as an intended user, you can no longer access that particular the subject of the attack.
An example scenario:
If a website you regularly use – maybe even your own website – is hit by a DoS attack, the website's resources are tied up so that users cannot access the site at all.
There are two types of DoS attacks:
- Flooding Attacks: This is commonly used by cybercriminals who flood a particular system with a huge amount of traffic, overwhelming the server. The end result is that the system gives up and stops functioning.
- Crash Attacks: These are not as common as flooding attacks, and involve cybercriminals infecting a system with bugs. This results in the system crashing. Legitimate users can no longer use an online service such as email, their bank account, or other crucial sites.
The first documented DoS attack is attributed to "mafiaboy," a 15-year-old Canadian hacker who launched a series of attacks against big ticket ecommerce providers such as eBay and Amazon.
What are DDoS attacks?
DDoS attacks are a more complex and evolved version of DoS attacks – and these are likely to increase in the future.
The key difference between a DoS and DDoS attack is that in the former, superfluous requests are sent to the system from a single source (a single computer and a single IP address). Alternately, in the latter, illegitimate requests are sent to the system from multiple sources. The very fact that DDoS attacks are launched from multiple locations makes them extremely difficult to detect and stop.
DDoS attacks is similar to a DoS attack wherein it aims to flood a server, service, website, or network with internet traffic. However, the method of executing these attacks differs from DoS attacks.
Here, a network of hacked computers (bots), also called "zombie computers," are used to form a network of bots or a botnet, which is then leveraged to send huge quantities of illegitimate data to servers, websites, and networks to bring them down.
The reason why DDoS attacks are considered so dangerous is because attackers can use millions of computers to launch an attack Mitigating these attacks is a huge challenge.
The first DDoS attack happened in 1999, when 114 computers were "pressed into service" by cyber attackers to launch an attack on a computer at the University of Minnesota.
Why should you be concerned?
As individuals, we typically aren't concerned about these attacks because big businesses face the brunt of them. But this doesn't mean your PC or Mac won't become compromised and be used as a part of these attacks – and you may never know about it.
This is why it's not only important that you are aware of how such attacks might misuse your computer, but also take steps to protect your computer.
Protection is the better part of valor
It's so important to maintain good cyber hygiene. Avoid visiting sites that are a hotbed for malicious activities. Also, make sure you only download files from trusted sources. It's important to keep your software up to date to fix any vulnerabilities that criminals might exploit.
But that's not the end of it. You must deploy an antivirus solution that offers end-to-end security against the most advanced threats against your Windows PCs, Macs, iPhones, iPads, and Android phones.
Sophos Home offers all the security and privacy you need. Delivered through a single user-friendly product, Sophos Home scans your computer for hidden threats and gets rid of all malware it detects, including viruses, spyware, rootkits, trojans and more. With its AI threat detection, malware both known and unknown is kept at bay. Plus its exhaustive privacy protection ensures cybercriminals cannot capture what you're typing by encrypts all keystrokes.
With Sophos Home, you make it difficult for cybercriminals to gain unauthorized access to your computer and make it a part of a botnet that launches a DDoS attack.